TIGTA: IRS Failures on Cybersecurity, Modernization, & Support System Protection
Yeah, you read that correctly. The Treasury Inspector General didn't have much positive to say.
In three of their latest reports, TIGTA (The US Treasury Inspector General for Tax Administration) has not had positive notes or comments. TIGTA is, essentially, the independent auditors of the IRS and its systems. They review initiatives, efficiency, security, impact, guidance, and more. Ultimately, if you want to know what is really going on with the IRS, this is the organization to follow.
TIGTA gave the IRS red marks in cybersecurity, modernization of legacy systems, and protection protocols in place on support systems. It’s been a bad week for the IRS. But, have no fear, we are here to break it all down.
Report 1: The IRS’s Cybersecurity Program Isn’t Effective
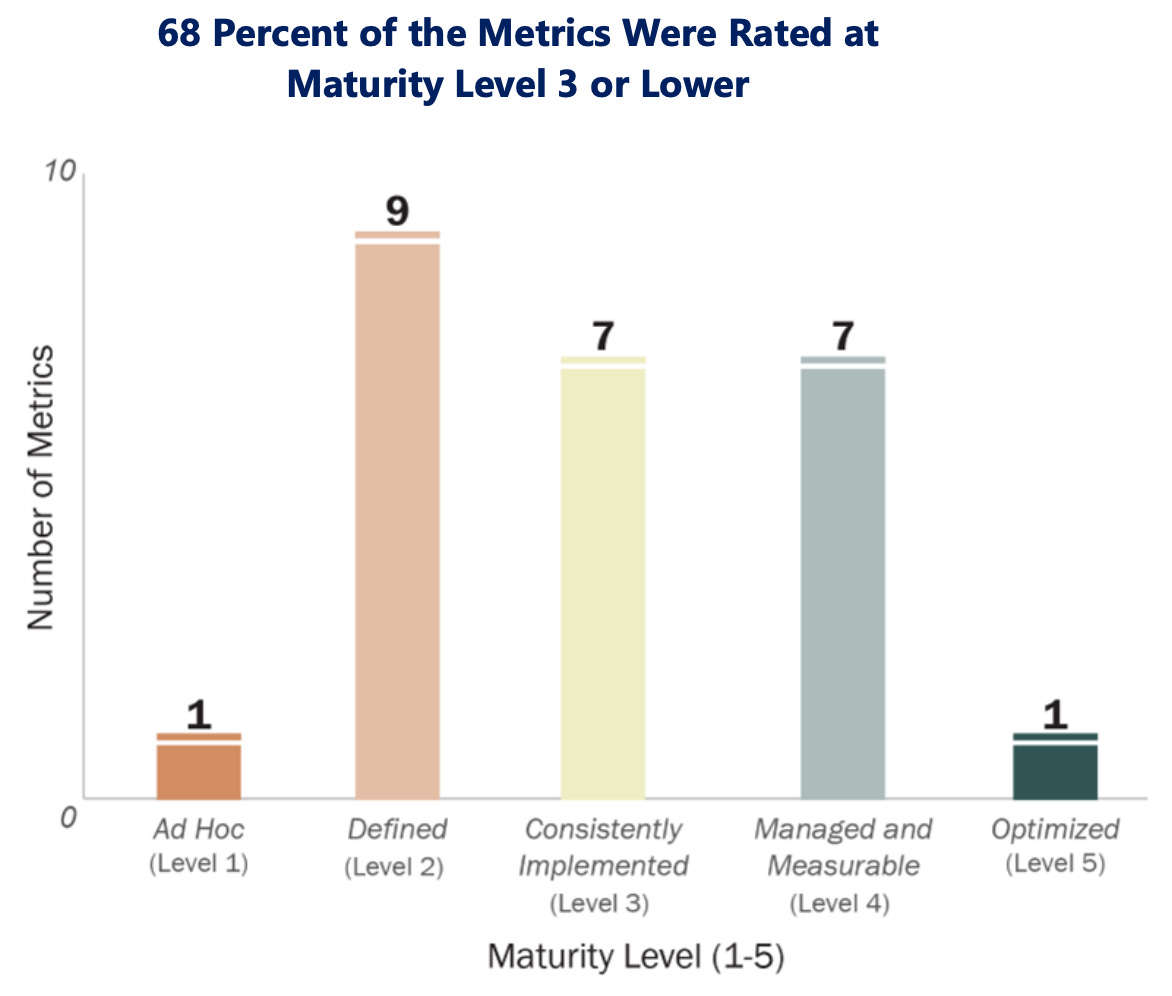
TIGTA has established 20 core items (or metrics in their terms) that they test, track, and report for security within the IRS. For each one off these, they are assigned a maturity level from 1 to 5 (with 1 be low or ad-hoc needs and 5 being ideal or optimized). Over two-thirds of the metrics received a three or lower, deeming them not sufficient.
But there is more to the story. The IRS has to comply with FISMA (The Federal Information Security Modernization Act) which sets the standards for security and technology oversight for federal agencies. FISMA is not just for the IRS, but all federal agencies. One of the requirements of FISMA is an independent annual audit of security.
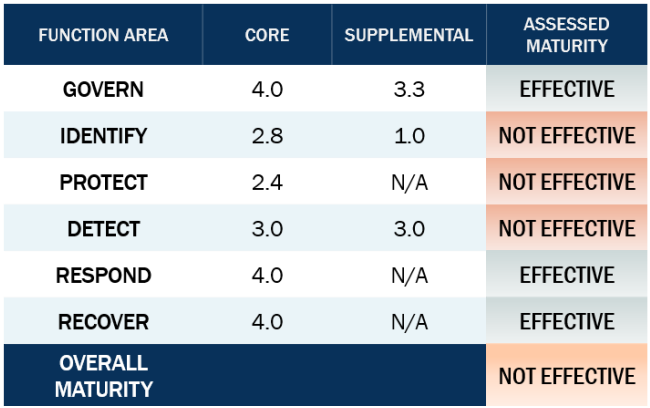
Upon audit, three of the six functional areas of cybersecurity were deemed “Not Effective.”
Govern is the policy and process stage, and the IRS was deemed to have effective policies. Similar, and very closely related to Govern, Respond and Recover scored well as these are the stages of how to respond to a situation or event.
However, the IRS did not score well on identity threats, protecting against threats, nor detecting threats. These three areas are the execution areas of security. What does this mean? The IRS is good at talking about security, but is not good at implementing.
The report provided a large list of corrective actions that the IRS will now have another year to implement and improve.
Note: This report is a great read as it highlight both digital and physical elements of the IRS plans and procedures. In many cases, the physical attributes are sometimes forgotten with small firms in an attempt to focus on the digital security.
Report 2: Failure to Decommission Legacy Tools
Looking for a one-line summary of this report? “The IRS is a hot mess.” Ok, but joking aside, five years ago, TIGTA issued a report stated that the IRS didn’t have a plan to decommission (or shut down) legacy systems. This led to a 2022 policy to decommission which failed do to lack of internal prioritization. In 2024, the IRS issued an updated process that included no process to decommission. During their recent audit, TIGTA discovered that 63% of the case management systems at the IRS were deemed legacy and should be decommissioned. As an impact on their failure to do so, $39 million was spent in 2024 maintaining these systems. Until corrective actions are taken, this uncontrolled expense will continue.
Many fingers were pointed in blame-shifting but let’s be honest. It’s a mix of broken systems, continual change in leadership, lack of prioritization, and lack of resources. In this situation, there is no single point of failure or blame.
The IRS has met with TIGTA and has agreed to prioritize the decommissioning of these systems. No deadline was set.
Report 3: Support Systems Are Not Protected
The IRS was also determined to be non-compliant with their security requirements connected to their support platform. While TIGTA did provide credit for improvement since the last report, it was still stated that significant vulnerabilities exist.
The largest concern is that physical IRS servers are lacking appropriate configuration and are currently open to exploits through known vulnerabilities. In fact, their client-facing (production) servers were found to be lacking basic protection. The items lacking were redacted, but the typical types of protection in these cases would be standard firewalls, anti-virus, etc.
TIGTA provided five steps for remediation, but they are all high-level and generic. Sadly, given the other priorities the IRS currently has, we do not anticipate this item being removed the report next year.
The Sad State of Affairs
I am sitting here and I honestly feel bad reporting this today. I have almost no improvement or positive news to report. Most of these reports are almost word-for-word the same as previous reports. The IRS is in a technology rut.
However, each firm is accountable for their own actions. Just because the IRS is unable to meet these standards, firms should not assume that they would not be held accountable. It is the old “do as I say, not as I do.” :-/
If you do not fully understand an issues or if you need assistance working through a resolution, the team here at Financial Guardians is available for Individual Support Calls to assist with any individual or specific matters.
Financial Guardians has partnered with NAEA to provide access to our monthly Guardian Tier membership at a 30% discount.
Active NAEA members can access the online discount here.
Financial Guardians is a proud member of InCite, the recently launched online community exclusively for tax professionals, bookkeepers, and accountants. InCite members receive a 30% discount.
Join today at www.incite.tax.
Financial Guardians has partnered with the California Society of Tax Consultants to provide a 30% access discount as well as many other offers. More info can be found at www.cstcsociety.org